hi there
Get an amaazing Domain Authority score above 50 for your website and
increase sales and visibility in just 30 days
https://www.str8creative.co/product/moz-da-seo-plan/
Service is guaranteed
Regards
Mike
Str8 Creative
support@str8creative.co
27 December 2020
Get Guarnateed DA50+ for %domain%
23 December 2020
re: I need to make a website`s ranks go down
hi
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
20 December 2020
Our most powerful SEO Ultimate Plan
hi there
Getting Top 10 Position in Search Engines is a Must for every Website if
you are really serious to do Online Business. If you are not in !op 10 it
means you are getting only 5% of visitors for that particular keyword.
Please find more information on our plan here:
https://str8creative.co/product/seo-ultimate/
thanks
Ikisha
support@str8creative.co
09 December 2020
re: Rank top 5 in the Google maps
hi there
Did you know that when someone is looking for a search term on their
phones, the Gmaps listings its what pop up first in the results?
Stop losing all that visibility and let us boost your G listing into the
tops for local terms
https://www.str8creative.co/product/1500-gmaps-citations/
thanks and regards
Mike
support@str8creative.co
05 December 2020
Blackhat tactics for ranking fast
hi
The most powerful & tested positive SEO packages available today. Designed
to rocket you to the top of Google.
https://bns-advertising.co/affordable-seo-services-small-businesses/
for further information please email us here
support@bns-advertising.co
thanks
Peter
01 December 2020
Guaranteed Domain Authority 50/100
hi there
Here is how we can do it
https://www.str8creative.co/product/moz-da-seo-plan/
Regards
Mike
Str8 Creative
support@str8creative.co
27 November 2020
re: I need to make a website`s ranks go down
hi
Yes, it is possible, with our service here
https://negativerseo.co/
for further information please email us here
support@negativerseo.co
thanks
Peter
21 November 2020
Cheap Monthly SEO plans %domain%
hi there
After checking your website SEO metrics and ranks, we determined that you
can get a real boost in ranks and visibility by using any of our plan below
https://www.cheapseosolutions.co/cheap-seo-packages/index.html
cheap and effective SEO plan
onpage SEO included
For the higher value plans, DA50 DR50 TF20 SEO metrics boost is inlcuded
thank you
Mike
support@cheapseosolutions.co
20 November 2020
re: need unique domains backlinks
hi there
Do you mean that you want 1 backlinks from 1 domain? unique domains links
like this?
yes, we offer that here
https://str8creative.co/product/unique-domains-links/
thanks and regards
Mike
support@str8creative.co
27 October 2020
fw: blog EDU backlinks
hi there
1000 Edu blog backlinks to improve your backlinks base and increase SEO
metrics and ranks
http://www.str8-creative.io/product/edu-backlinks/
Improve domain authority with more .edu blog backlinks
Unsubscribe from this newsletter
http://www.str8-creative.io/unsubscribe/
22 October 2020
Domain Authority 50 for your website - Guaranteed Service
We`ll get your website to have Domain Authority 50 or we`ll refund you every
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
28 September 2020
Domain Authority 50 for your website - Guaranteed Service
We`ll get your website to have Domain Authority 50 or we`ll refund you every
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
22 September 2020
Fun Art Projects
I've not been in the mood to write articles lately, so instead I've been working on some fun projects instead. Watabou posted about Dyson Hatching, which got me thinking it might be interesting to constrain the hatch lines to Voronoi cells. I implemented that and then got carried away with colors, line spacing, line width, and other fun things. The demo is here. You can drag an image onto the diagram to use the colors from your image.
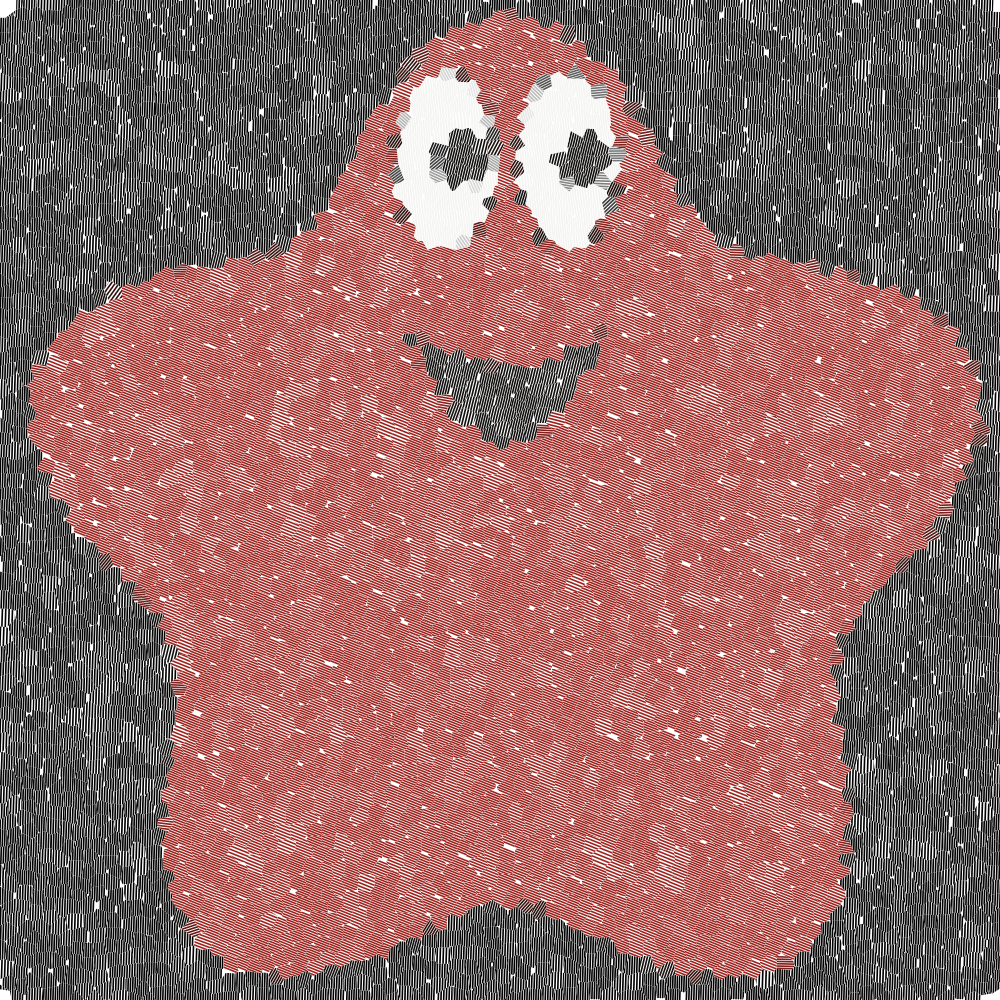
The second project was also thanks to a Watabou tweet. It inspired me to play with shaders on a Delaunay mesh. Once again I got carried away and had lots of fun making patterns. The demo is here. Play with the first two sliders to pick the pattern, then adjust the other sliders to fine tune it.

Enjoy!
21 September 2020
The Gotek Floppy Drive Emulator In The IBM PC World
The Gotek floppy drive emulator is a simple, cheap and little device that, as its name says, emulates a floppy drive. There are many varieties of these devices and they usually come with a USB port on the front of the unit and a 34-pin header + 4-pin power header on the back. While originally intended to replace disk drives in industrial, sewing and musical equipment, they can be used with standard PC floppy controllers. However, as they come they are at best diamonds in the rough, so in this blog entry I will describe how to make these devices more useful for vintage IBM PCs and compatibles.
Read more »
17 September 2020
1500 google maps citations cheap
Rank the google maps top 5 for your money keywords, guaranteed
http://www.str8-creative.io/product/1500-gmaps-citations/
regards,
Str8 Creative
12 September 2020
Goblyn Head Press News
You may or may not know this, but I own a very small game publishing company. How small? Well... so far we have produced exactly three items for sale, and all of those have been released in the past month.
To date, Goblyn Head has produced a supplement for D&D 5e, and adventure for 5e, and a generic map of a barrow mound that is free to download ("Pay What You Want"). All are available from DriveThruRPG here.
Come check it out! Zeebs (our mischievous but friendly goblyn mascot) will show you how to go. And if you do pick up something, please leave a review!
Why Is K.I.S.S.ing So Hard?
Keep It Simple Stupid!
I did get a chance to try my "improved", more 'accurate', less 'gamey' version of the rules and once again by the time the game was over, it was tedious, bordering on boring actually, and taking far too long for a quick solo game. (Please imagine a clever gif of me scrounching up a piece of paper and dunking it in a waste basket.)
So I did what works best for me. I did other things for a while (including a 16thC game over Hangouts where I was rightfully trounced - sorry no pics but I expect the game will appear on the Sharp Brush blog.).
Then, today, I came back with a fresh eye and an open mind.
 |
| Once more unto the Bridge! Turn 8ish of 15: the armies are all on board and well engaged. |
The first step was to spend some time with my nose in books. Then, I let my subconscious mind guide me as I poked at the figures and started to think of other mechanisms, "the look of the thing", what needs to be shown and what doesn't and about the sorts of decisions I want to be making as a player.
 |
| Casualties mount. The Bodyguards charge into the battered grey infantry! |
The next thing was to again regroup the figures into units of 8 infantry or 4 other figures which is how they are painted. I then dumped the existing command control and activation rules, the fiddlyier bits, the existing morale rules, the mutiphase charge resolution and the proposed reintroduction of pinned and rally rules.
I then scribbled some note outlining the new simple game, tweaked it once or twice for things that arose mid game, and played an engaging, very close, occasionally nail biting, rematch of the same OHW scenario in roughly an hour.
The details are more abstracted but then so are the shiny toys and the things I had to think about as player seemed to me more like things a General should be thinking about.
 |
| Turn 13/15. The Hochelaga Fusiliers are the last fresh Dominion unit. "Fix Bayonets" "CHARGE!!" and the last remnants of shaken rebel units flee over the bridge. Another incursion has been repulsed. |
So, that's one happy test game. The rules have been amended to match and the link posted on my Rules blog page.
I think its time to do some casting and painting and the like, and then try it again with a bigger scenario and more men!
07 September 2020
Domain Authority 50 for your website - Guaranteed Service
We`ll get your website to have Domain Authority 50 or we`ll refund you every
cent
for only 150 usd, you`ll have DA50 for your website, guaranteed
Order it today:
http://www.str8-creative.co/product/moz-da-seo-plan/
thanks
Alex Peters
04 September 2020
Download Tekken 6 Full Version For Pc
Tekken 6 Full Review
System Requirements of Tekken 6 For Windows PC
- Operating System: Windows XP/Vista/ Windows 7 ( 64 Bit )
- CPU: Intel Pentium 4 or later.
- Setup Size: 700 MB
- RAM: 1GB
- Hard Disk Space: 1GB
31 August 2020
Hacking Everything With RF And Software Defined Radio - Part 2
YardStick One Unleashed, Automating RF Attacks In Python - An RFCat Primer
Twitter: @Ficti0n
Site: cclabs.io or consolecowboys.com
Purchase Devices needed to follow this blog series:
Target 1:(from the last blog)Video Series PlayList Associated with this blog:
The first thing we did in our last blog after looking up the frequency was to open up GQRX and check if we can see our devices signals. As it turns out you can actually do this in python with RFCat. Which is really convenient if you left your Software Defined Radio dongle at home but happen to have access to a Yardstick.
RFCat as a Spectrum Analyzer:
Sniffing RF Data With The YardStick and Python:
TroubleShooting Antenna Issues:
- When using a telescopic antenna closed I had almost repeating output with some random bits flipped
- When extending the antenna it went crazy output with random noise
- I then used a small rubber ducky antenna and got the repeating output shown above.
What we have done so far:
- Verify the frequency with RFCat
- How can I listen for it and capture a transmission with RFCat
- How can I send this transmission with RFCat
Using RFrecv() for Listening:
Parsing and replaying data:
- We need to parse out the data from the surrounding 0s
- We need to convert it to a format we can send (tricker then it sounds)
- We need to add padding and send that data over (We know how to do this already)
Parsing Data:
Data Format Woes:
Formatted Hex Vs Manually Pasted Hex
- Your encoded capture
- Your parsed payloads in a nice list
- Your payload being processed into hex.
- Your nicely formatted Hex created by your code above (Yay for us)
- Then you have your manually pasted in hex from your original attack payloads as unprintable characters (What?)
BitString BitArray Formating FTW:
Note: I sent similar code to a friend and had him run it against a black box real world target. He had permission to attack this target via the owner of a facility and it worked flawlessly. So although a doorbell is a trivial target. This same research applies to garages, gates, and any other signal not using protection mechanism such as rolling code, multiple frequencies at once etc.
Thats All Folks, Whats Next:
Continue reading
- Hack Tools For Windows
- Pentest Box Tools Download
- Easy Hack Tools
- Pentest Tools Subdomain
- Hacking Tools
- Pentest Tools
- Hack Tools Download
- Pentest Tools Port Scanner
- Pentest Tools Tcp Port Scanner
- Pentest Reporting Tools
- Hack App
- Computer Hacker
- Pentest Tools Linux
- Hack Tools Github
- Hack Website Online Tool
- Game Hacking
- Pentest Tools Online
- Usb Pentest Tools
- Termux Hacking Tools 2019
- Hack Tools Online
- Hacking Tools Hardware
- Pentest Tools Github
- Easy Hack Tools
- Tools For Hacker
- Hacking Tools For Mac
- Hacker Tools For Ios
- Underground Hacker Sites
- Computer Hacker
- Hacker Tool Kit
- Pentest Tools Subdomain
- Pentest Tools Free
- How To Make Hacking Tools
- Hacker Tools Hardware
- Nsa Hack Tools
- Pentest Tools Port Scanner
- How To Hack
- Hacking Tools
- Pentest Tools Github
- Hack Tools 2019
- Pentest Tools Open Source
- Pentest Tools Free
- Pentest Tools Review
- Hacking Tools Free Download
- Pentest Tools Online
- Hacking Tools For Mac
- Hacking Tools 2020
- Hack Tools
- Hack Tools Online
- Pentest Tools For Ubuntu
- Termux Hacking Tools 2019
- Hacking Tools Free Download
- Pentest Tools Find Subdomains
- Hacking Tools For Beginners
- Bluetooth Hacking Tools Kali
- Hacker Tools 2019
- Tools Used For Hacking
- Hacking Tools Usb
- Hack Tools For Pc
- Hacker Tools Free
- Hack Website Online Tool
- Termux Hacking Tools 2019
- Hacking Tools For Kali Linux
- Hacker Tools For Pc
- Hacker Security Tools
- Pentest Tools Nmap
- Github Hacking Tools
- Hacking Tools Online
- Hacker Tools Linux
- Hack Tools
- Pentest Tools Subdomain
- Best Pentesting Tools 2018
- Bluetooth Hacking Tools Kali
- Pentest Tools Android
- Hacking Tools And Software
- Hacker Tools Software
- Pentest Tools Open Source
- Hacking Tools Mac
- Install Pentest Tools Ubuntu
- Hacker Tools For Pc
- Nsa Hack Tools
- Pentest Tools Kali Linux
- Hack Rom Tools
- Hack Tools Github
- Hacking Tools For Pc
- Computer Hacker
- Hacker Tools 2019
- Hacker
- Hacking App
- Best Pentesting Tools 2018
- Hacking Tools For Games
- Pentest Tools Website Vulnerability
- Hacking Tools For Mac
- Hacking Tools Free Download
- Nsa Hacker Tools
- Pentest Reporting Tools
- Hacking Tools Name
- Hack Tools For Mac
- Tools Used For Hacking
30 August 2020
WordPress 5.0.0 Crop-Image Shell Upload Exploit
Related articles
- Hack Tools
- Hack Tools For Pc
- Ethical Hacker Tools
- Hacking Tools Windows 10
- Android Hack Tools Github
- Pentest Reporting Tools
- Hacking Tools Name
- Hacker Search Tools
- Growth Hacker Tools
- Hacks And Tools
- Pentest Tools Port Scanner
- Pentest Tools Alternative
- Hacking Tools Windows
- Hack Tools
- Top Pentest Tools
- Pentest Tools Online
- Pentest Tools Kali Linux
- Hacker Security Tools
- Hacking Tools Name
- Pentest Tools Nmap
- Pentest Recon Tools
- Pentest Tools For Ubuntu
- Hacker Tools 2020
- Android Hack Tools Github
- Hackers Toolbox
- Hacker Tools Online
- Hackrf Tools
- Pentest Tools For Mac
- Hacking Tools Mac
- Hak5 Tools
- Hacking Tools For Games
- Growth Hacker Tools
- Hacking Tools For Beginners
- Best Hacking Tools 2020
- Physical Pentest Tools
- Pentest Tools Nmap
- Pentest Tools Tcp Port Scanner
- Hacking Tools Mac
- How To Make Hacking Tools
- Hacker Tools 2019
- Hack Tool Apk
- Hacking Tools Kit
- Pentest Tools List
- Pentest Tools Download
- World No 1 Hacker Software
- Pentest Tools For Mac
- Hacker Tools Github
- Nsa Hack Tools
- Hackrf Tools
- Hack Tools
- Hack And Tools
- Hacker Tools For Windows
- Hacking Tools For Windows 7
- Nsa Hack Tools
- Pentest Tools Website
- Pentest Automation Tools
- Hacker Tools 2019
- Hak5 Tools
- Hacker Security Tools
- Pentest Tools Framework
- Pentest Tools Port Scanner
- Hacker Tool Kit
- Pentest Tools Linux
- Hacker Tools Software
- Black Hat Hacker Tools
- New Hack Tools
- How To Hack
- Hacker Tools 2019
- What Is Hacking Tools
- Pentest Tools Url Fuzzer
- Free Pentest Tools For Windows
- Pentest Tools For Ubuntu
- Hacker Tools 2020
- Hacking Tools Kit
- Hacking Tools Windows 10
- Hacking Tools Windows
- Hacker Tools For Ios
- Game Hacking
- Hacking Tools Usb





















